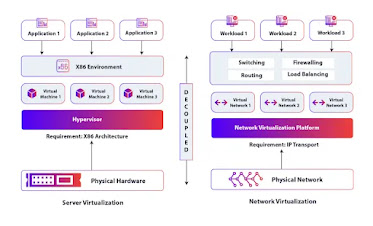
Network virtualization is a process of separating the functions of a network into different components, such as the physical infrastructure and management and control software and allowing those functions to operate separately. In this process, the software is used to emulate the functionality of hardware components that are commonly part of a traditional network.
Network services are decoupled from the physical hardware they run on. They can be used independently, making them perfect for any network device. With this shift to programmable networks, we can more flexibly provision networks, more securely manage them, and programmatically and dynamically manage them.
Network virtualization simplifies life for network administrators by making it easier to move workloads, modify policies and applications, and avoid complex and time-consuming reconfigurations when performing these tasks. In addition, customers and business people need instant access to various content, services, and information.
Network virtualization results from network virtualization software, which simulates the presence of physical hardware, like routers, switches, load balancers, and firewalls. In layman’s terms, a network virtualization implementation may virtualize components spanning multiple layers of the Open Systems Interconnection Model. These include ones at Layer 2 (switches) and Layer 4 and beyond (load balancers, firewalls, etc. So, for example, in an SD-WAN solution, you can manage your virtual appliances using a management tool.
Network virtualization software creates virtual representations of a network’s underlying hardware and software. This enables you to combine virtualized representations of underlying hardware and software into a single administrative unit. A virtualized environment allows the resources to be hosted inside virtual machines (VMs) or containers and run on top of off-the-shelf commercial x86 hardware to reduce costs. Network virtualization is a technology that allows for workloads to be deployed over a virtual network. Current network policies ensure that the correct network services are coupled with each VM- or container-based workload.
Services move dynamically as workloads come and go, while police change their configuration is a snap. As a result, virtual networking is closely related to SDN, SD-WAN (a subtype of SDN), and network functions virtualization (NFV).
SDN stands for programmable networks, and while it is still in the research phase, it shows tremendous potential for enhancing security, performance, and scalability. For example, one recent report suggested that by 2025, 40% of global Internet traffic will be handled via SDN. As for SD-WAN, it’s an example of the types of network overlays you can achieve with network virtualization.
What are the different types of network virtualization :
There are two broad categories of network virtualization: External and internal network virtualization.
External network virtualization
The goal of the external network virtualization is to allow for seamless interoperation of physical networks and thus allow for better administration and management. Network switching hardware and virtual local area network (VLAN) solutions are used to create a VLAN.
In this VLAN, hosts attached to different physical LANs can communicate as if they were all in the same broadcast domain. This type of network virtualization is prevalent in data centers and large corporate networks. A VLAN may separate the systems on the same physical network into smaller virtual networks.
Internal network virtualization
Network virtualization entails creating an emulated network inside an operating system partition. The guest VMs inside an OS partition may communicate with each other via a network-like architecture, via a virtual network interface, a shared interface between guest and host paired with Network Address Translation, or some other means. Internal network virtualization can help prevent attacks on your internal network by isolating applications that might be vulnerable to malicious threats. Networking solutions that implement it are sometimes marketed as “network-in-a-box” offerings by their vendors.
This technology can take many forms.
Standard VLAN technology is still vital, but its limited 12-bit structure has led to the development of better, technically advanced alternatives, particularly when it comes to multi-tenant cloud computing. Virtualization in cloud architectures relies upon multiple types of virtualization to create centralized, network-accessible resource pools that can be quickly provisioned and scaled.
- It is increasingly possible to provide cloud-based services to software-defined data centers and the network edge with network virtualization. The successors to VLAN are:Virtual Extensible Local Area Networks (VXLANs) can be deployed in Software-Defined Wide Area Networks (SD-WANs).
- The 24-bit Network Virtualization using Generic Routing Encapsulation (NVGRE).
- The 64-bit Stateless Transport Tunneling (STT).
- Generic Network Virtualization Encapsulation (GENEVE) is a standard that doesn’t specify any particular configuration or set of specs.
What are the benefits of network virtualization :
Once implemented, network virtualization delivers higher speed, automation, and administrative efficiency than achievable with only a physical network, for example, a traditional hub-and-spoke WAN. These advantages translate into concrete operational benefits for enterprise businesses and service providers, including but not limited to:
Superior network agility and application delivery
Virtualizing networking enables you to scale networks while maintaining the flexibility of an infrastructure solution. Keeping up with demand for virtual, cloud, and SaaS applications requires an agile, dynamic, and flexible network environment.
This goal requires network virtualization, which reduces the time it takes to deploy a network from days or weeks to just minutes and makes the network more flexible and adaptable. One way to do this is by using an SD-WAN overlay, which provides an always-on network that dynamically steers traffic from datacenters, branches, clouds, and SaaS.
Streamlined network administration and management
Virtual networks are more straightforward to set up than their physical counterparts. Network administrators now have more options than ever for automating changes to virtual networks. Workloads running in VMs can move through the web without any configuration for proper application mobility. Just as with a branch of an SD-WAN, new components added to an MPLS VPN can be automatically provisioned (zero-touch provisioning) with the correct policies and updated centrally.
Stronger security
Datacenter security and network virtualization are vital additions to datacenter security. Separating the physical network from the virtual network isolates the physical network from any virtual network. This is also the case between different virtual networks. The principle of least privilege is a way to ensure that network security is enforced for the appropriate user and purpose. As data centers become more extensive and complicated to manage, it is becoming increasingly essential to virtualize network services and consolidate them across multiple servers. Citrix SD-WAN Orchestrator helps simplify and manage SD-WAN. It lets you integrate SD-WAN and cloud-based security gateways seamlessly and without compromising the user experience.
Website : sciencefather.com
See more Info : - network.sciencefather.com
Nomination : https://x-i.me/network
Registration : https://x-i.me/prireg2
Contact us : network@sciencefather.com
Social Medias :
Instagram : https://x-i.me/net23m
Pinterest : https://x-i.me/net23p
Facebook : https://x-i.me/net23f
Linked in : https://x-i.me/net23l
Youtube : https://x-i.me/NQGu
#ScienceFather #ResearchAwards #NetworkVirtualization #NetworkProtocols
#Communication #Networking #Impromptu #Technology #Ad Hoc
#VirtualNetworks #SDN #SoftwareDefinedNetworking #NFV
#NetworkInfrastructure #VirtualizationTechnology #CloudNetworking
#VirtualizationSecurity #NetworkOverlay #NetworkManagement



No comments:
Post a Comment